Ad Build Large-Scale Services with Azure Virtual Machine Scale Sets. Single series all timeline.
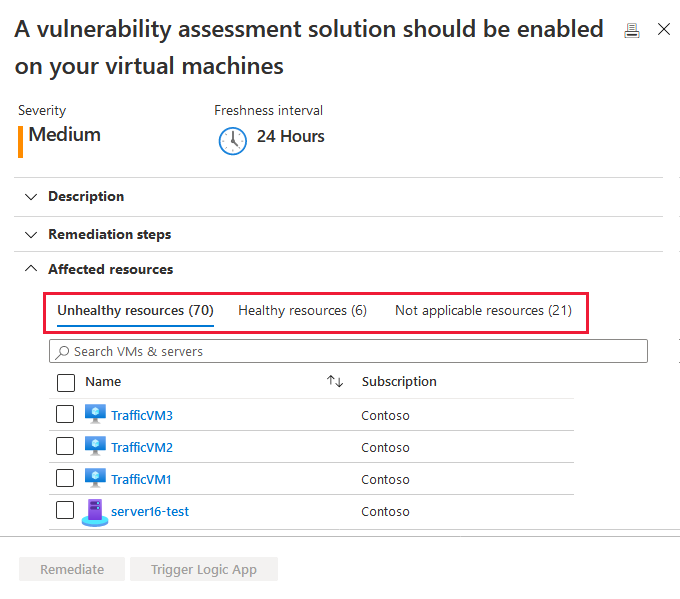
Byol Vm Vulnerability Assessment In Microsoft Defender For Cloud Microsoft Docs
I believe I am only different from you in.

. N7 3 Nov 2021 by Duty Mastr Details. We currently package our virtual machines for four different virtualization software options. VirtualBoxs import dialog will launch.
OP specifically asks for vulnerable windows images to use in a testing environment. Damn Vulnerable Web Application is damn vulnerable. Do not upload it to your hosting providers public html folder or any Internet facing servers as they will be.
Typhoon Vulnerable VM is a virtual machine bundled with several vulnerabilities that provides a laboratory environment for researchers looking into enhancing their skills in the field of Cyber. VulnHub provides materials allowing anyone to gain practical hands-on experience with digital security computer applications and network administration tasks. Theyre absolutely free for 90 days and then you rearm load the saved snapshot or reinstall for.
HackMyVM and Vulnhub are free to use and you have to download. Download a virtual machine. If you want to change the machines name or description you can do it by double-clicking on the values.
Ad Build Large-Scale Services with Azure Virtual Machine Scale Sets. We will name it vulnerable_vm and leave the. So there are many platforms out there like HackMyVM Vulnhub HackTheBox and TryHackMe to name a few.
Download Metasploitable the intentionally vulnerable target machine for evaluating Metasploit. It can sometimes be challenging to find vulnerable machines for your penetration testing or vulnerability management lab. Escalate_Win - A intentionally developed windows vulnerable virtual machineThe main focous of this machine is to learn Windows.
Heres a list of vulnerable machines you should check. Ive been fighting with this for some time my Win7 VM environment is not vulnerable to the smb vulnerability EternalBlue exploit. VMWare Hyper-V VirtualBox and Parallels.
Taking your first steps with Metasploit can be difficult especially if you dont want to conduct. The end goal is to go from zero access on the system all the way to root access. Vulhub is a website that contains a massive collection of vulnerable virtual machines.
Post Exploitation Privilege Escalation Techniques.

A Survey On The Security Of Virtual Machines

Metasploitable Intentionally Vulnerable Machine Vulnerability Intentions Machine

What Is The Difference Between Physical Servers And Vms

Isolated Environment An Overview Sciencedirect Topics

Virtual Machine Monitor An Overview Sciencedirect Topics

A Survey On The Security Of Virtual Machines

0 comments
Post a Comment